VMware Aria Operations for Applications (formerly known as Tanzu Observability by Wavefront) supports both role-based control that use global permissions and object-based access control for individual dashboards and alerts.
Users with the Accounts permission can:
- Create roles with permissions and assign roles to users or groups.
- Protect individual dashboards or alerts and grant access only to selected groups or accounts.
- Protect metrics or groups of metrics by using metrics security policy rules.
Role-Based Access Control with Global Permissions
Permissions always apply to all objects of a certain type. For example, a user with Dashboards permission can view and modify all dashboards.
A user with Accounts permission manages authorization by:
- Creating one or more roles and assigning one or more permissions to each role.
- Creating one or more groups and adding one or more users to each group.
- Assigning one or more roles to each group.
Example
|
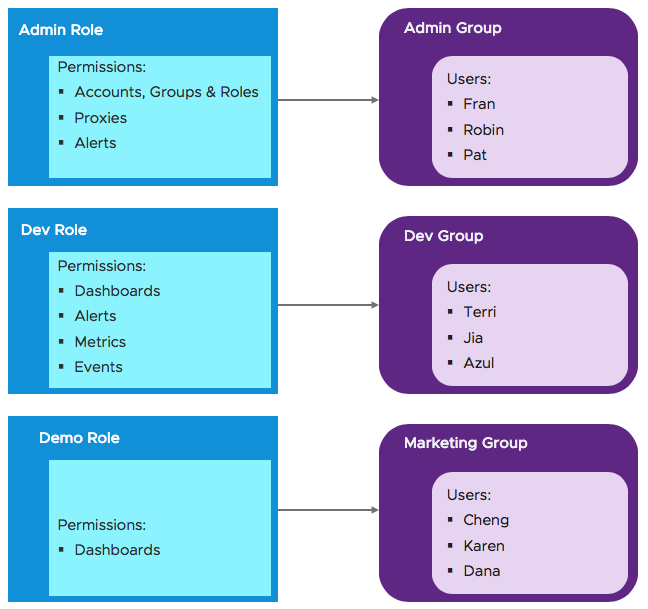
Users Get Permissions from Role
In this picture, we have 3 roles and 3 groups of users. Each user gets the permissions from one role. |
 |
|
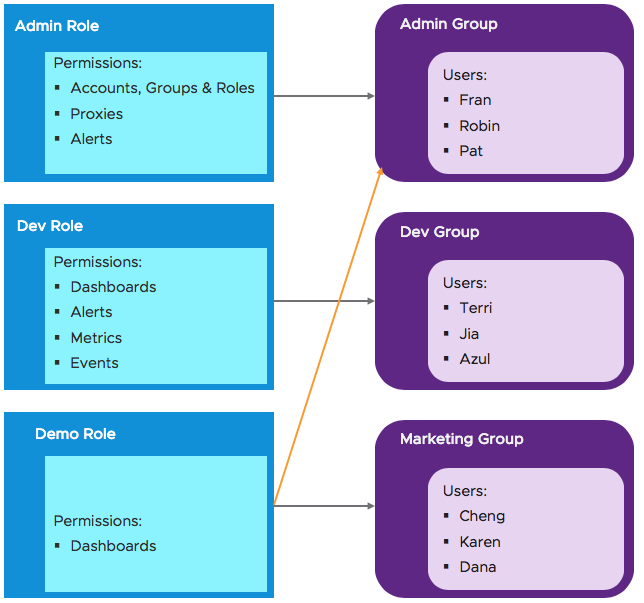
One Group with Two Roles
Management at the role and group level is less error prone, for example, it's easier to remove a role from a group than from 15 individual users.
|
 |
|
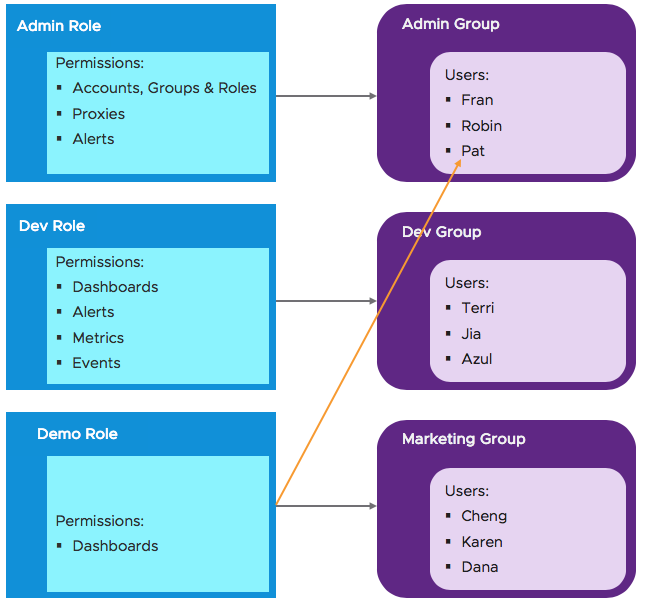
Individual User Permissions
Assigning roles or permissions to individual users is also supported.
|
 |
Access Control for Dashboards and Charts
Our fine-grained access control allows users with the Accounts permission to protect sensitive information, for example, to restrict access to certain dashboards to the Finance team.
- Access control on individual objects – While permissions are global and apply, for example, to all dashboards, access control allows you to restrict who can view or view and modify individual objects (initially dashboards and alerts).
- Security setting for new objects – In high security environments, users with the Accounts permission can set a security setting so that all new dashboards and new alerts are accessible only to the creator and to the Super Admin users.
Metrics Security Policy Rules
Any Super Admin user or users with Metrics permission can view, create, and manage metrics security policy rules.
Data protected by a metrics security policy rule can become completely invisible to users.
- Not visible in charts. The chart either includes a warning that some metrics are protected, or, if all metrics are protected, the chart shows only the message.
- Not visible in alerts (if Secure Metrics Details is checked for the alert). The alert fires based on the complete set of metrics, and the complete set is shown in notification images by default. A check box allows users with the Accounts permission to hide alert details so that confidential metrics are not shown.
- Not visible in auto-complete in Chart Builder, Query Editor, Metrics browser, etc.